Greetings friends,
After a long time, I wanted to share a little memory with you. I hope it will be an enjoyable article that you can read easily in a few minutes and will not tire you technically. :)
It was about 7-8 months ago. While walking home, my friend found a cell phone on the sidewalk at the beginning of the street. When he got home, he said he found a phone on the way, and we started talking about how we could get it back to its owner.
The options we found were:
- Handing over the cell phone to the police,
- Taking it to one of the shopkeepers in the vicinity,
- Waiting for the owner of the cell phone to reach us, or
- Looking for solutions that will allow us to reach the owner of our thoughts were, the phone :)
We have listed the order of the options from easy to difficult. Of course, when it comes to technical people, we prefer the last option, partly due to our nature. So we would find the owner of the phone! It sounds great, doesn’t it? But how! :)
We started to examine the phone:
- The phone was a smartphone with the Android operating system.
- The language of the phone was Russian.
- I don’t remember the brand, but it was one of the Chinese-originated brands.
- We couldn’t see the exact model information.
- Judging by the hardware, the phone looked around 3-4 years old.
- We charged the phone.
- We tried to start the phone:
- It had a SIM card PIN.
- We removed the SIM card.
- It had a screen lock. It is a screen lock where we enter a PIN with a PIN code, that is, a PIN consisting of numbers.
We completed the first phase, the review phase, and our findings were as above.
Now it was time to find the owner of the phone. (How would you find it if it were you? We will be looking forward to your answers.)
Our thoughts were:
- Bypassing the phone’s screen lock:
- Reaching the second number of the owner of the phone, if there is one in the contacts,
- Otherwise, calling or sending a message to one of the last incoming calls,
- Sending a message to one of the messages on the phone.
So how would we bypass the phone’s screen lock?
- As soon as I picked up the phone, I started trying the simplest and most commonly used PINs,
- Besides, I tried to understand if there was a measure such as a time-block, and yes, I could not enter a new PIN after 3 incorrect PIN attempts (PIN input field was closed to data entry and I had to wait for a certain time).
We call this prevention account-lockout (I’ll mention details below for those who are curious).
Therefore, we would not be able to overcome this part with the brute-force attack (I mentioned below).
So what else could we do?
- We could have tried to break the SIM lock of the phone and waited for the call to fall on the SIM, but this would be a little farther for us. Therefore, we turned our focus back to the phone.
- Then… a very simple but critical feature that I learned in 2018 came to my mind!
If the device’s WiFi is turned on, and it finds a passwordless modem nearby, it connects directly to that modem!
Isn’t it great?
Or do you say, “What does it have to do with?” Please don’t be impatient. :)
If the phone is connected to the modem, it is likely that the owner of the phone would have left an SMS to this number or a message to one of the messaging applications installed on this phone (WhatsApp, Telegram, etc.).
“But what happens if a message comes after you can’t unlock the screen?”, I seem to hear you say.
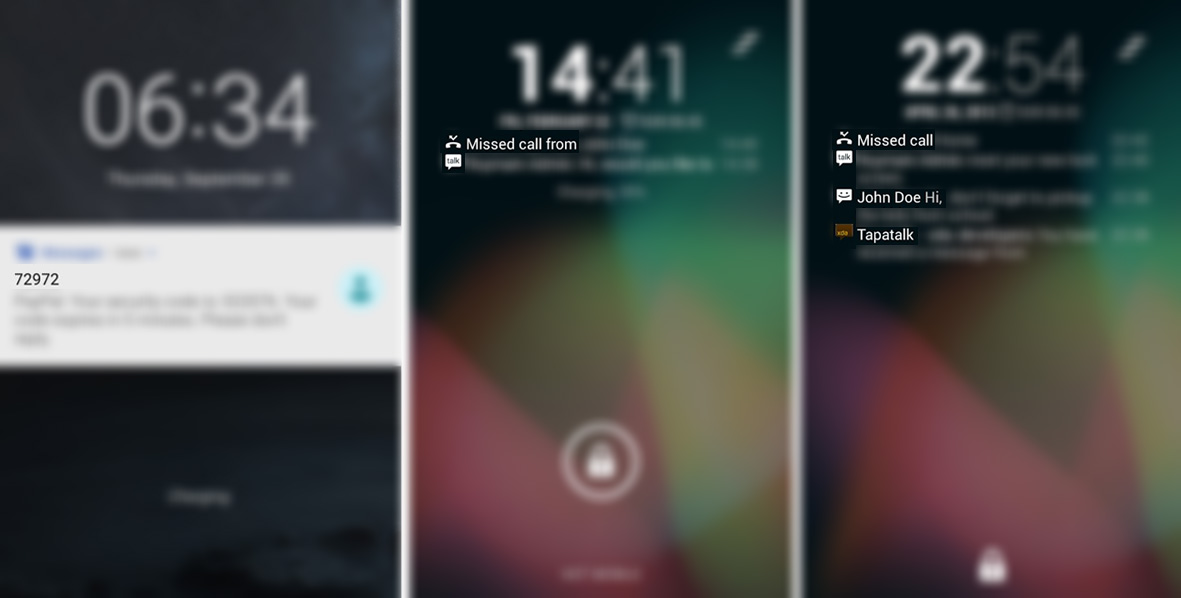
At this point, another feature would be a vulnerability for us. “What is it”, if you say; According to the default feature settings of Android devices, a notification coming to the phone can be partially displayed even if the screen is locked! (It is also possible to see the whole thing by swiping from above.) At worst, we would be seeing the first parts of the incoming notification – message on the wall.
So let’s get started! :)
We started the action:
- We immediately defined a guest connection without a password from the modem. And
- We pressed the power button on the phone and started watching what was going on with great excitement.
- And bingo! The phone was connected to the modem and notifications began to come one after another. Then…
- A message came to WhatsApp: Could you please leave the phone at X Hotel?
That’s it! We have reached our goal.. :)
For those wondering how we understood the message, the message was not in Russian, but in Turkish :) Of course, they sent the message in Turkish, since the person who found the phone on the road was much more likely to be a Turkish citizen. Because the story takes place in Turkey.
After learning the place to deliver the phone (this was a hotel quite close to home), my friend who brought the phone should have experienced this pleasure so he took the phone and set off.
My friend went to the hotel reception and said that he had found the phone and asked the receptionist friend to call the owner of the phone. The Russian couple who dropped the phone went down from their room with their children, and my friend confirmed that the couple who came in were the same people in the photo on the background of the phone. My friend delivered the phone, they thanked him, and we slept peacefully with this little joy :)
General notes and explanations for some of the parts mentioned above:
- This feature of auto-connecting to public WiFi on an Android phone, or the vulnerability in our example, is not unique to Android operating systems, of course, it is also valid in some Windows operating systems.
- If you ask for my suggestion, you can disable the auto-connect feature according to your operating system, or you can keep the WiFi connection of your phone/device turned off when you are outside of the safe zones (such as your home, office). In this way, the energy consumption of your phone will also be reduced.
- Let me answer as you will be wondering right away. If the phone was an iPhone, the phone would not automatically connect to this public WiFi because; This feature is turned off by default on iPhone devices.
- This feature is thought to be designed for the convenience of users, but as you have noticed, it is quite suitable for use as a security vulnerability. While it was lived for innocent benefit in our example, in a non-ideal world, someone could also use it for data theft (details in the next item).
- So, what’s wrong with our device automatically connecting to a public WiFi?
- Let’s start by addressing the most critical situation, if the internet access requests made from your device are not provided over SSL – HTTPS, that is, a secure connection, your requests can be monitored via the modem to which the device is connected!
- What if all requests are made over a secure connection called SSL – HTTPS, is there any privacy issue? Although not as much as in the first option, yes it still exists! This time, it is possible to monitor the server addresses that your device sends requests to – domain, that is, which sites it accesses.
- If you “say is that all?”, there is a little more like the package size of your request. Friends who want to go deeper into the work can do their research within the scenarios.As an alternative attack method, our target user may be exposed to a protocol-downgrade attack. How, if you say; If the SSL configuration is not done correctly on the relevant website, the attacker may send you your connection as http:// instead of https: and may cause your requests to continue without SSL – secure connection, and thus monitor all your internet activities.
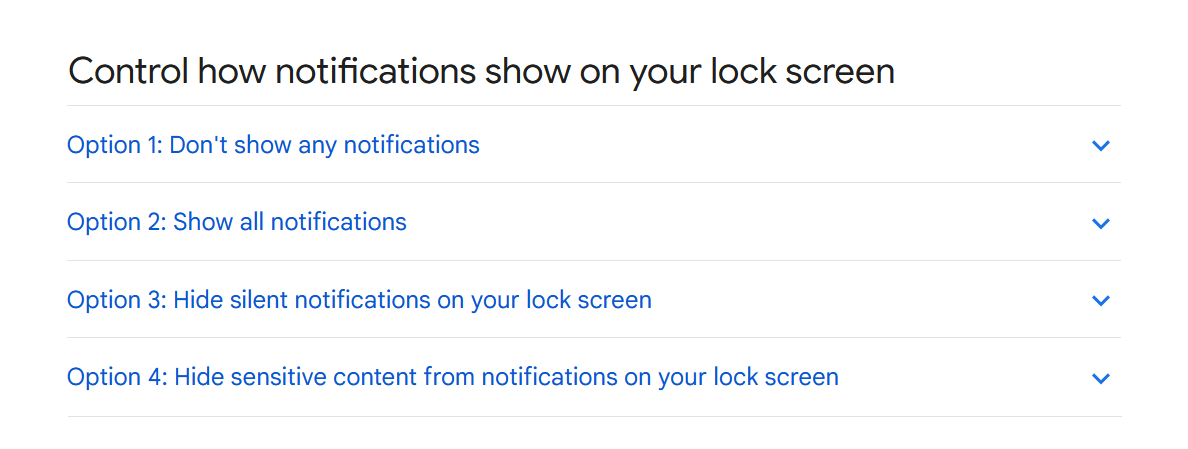
- Yes, notification contents on Android devices are turned on by default even when the screen is locked, so how can we hide these contents, the answer to the question > here it is.
Cross references:
- Brute-force attack: In this attack method, when the attacker does not have the key information of the targeted system, the method in which he tries to find the key by trial and error is called a brute force attack. In the example above, my attempt to unlock the phone’s PIN, such as 1234, 4321, 1212, in order, is an example of a brute force attack.
- Protocol-downgrade attack: Let’s get the full definition from Wiki, let me give an example.Wiki says for the definition of this attack:A downgrade attack, also called a bidding-down attack or version rollback attack, is a form of cryptographic attack on a computer system or communications protocol that makes it abandon a high-quality mode of operation (e.g. an encrypted connection) in favor of an older, lower-quality mode of operation (e.g. cleartext) that is typically provided for backward compatibility with older systems.Example: The link address of a website you are accessing is: https://site.com/tada. Again, if you can access this website as http://site.com/tada (non-SSL), a possible scenario is that an attacker will easily direct you to this link with a phishing message that will be sent to you and, according to the example above, they will be able to monitor your internet traffic.
- Account-lockout: There are two variants of this security measure. Soft-lock and hard-lock. Soft-locked is a temporary account lockout measure, while hard-locked; Permanent account lockout. If you say “Sahin, tell us about real life”. Now! Temporary locking of the screen in the scenario where you repeatedly enter the wrong mobile phone PIN or computer power-on password is an example of soft-locked, and hard-locked means that your account will be completely locked after 3 consecutive wrong entries to your bank account and can only be opened by bank officials. This is an example of a permanent lock.
Last word:
If you think that there is a wrong instruction in the information mentioned in the article, or if I were you, I would do this, friend! If there is a part that you say, please share your valuable ideas below, I wish you well.
Stay with love,
Safe days.
Thanks:
Thanks to Aysenur Burak for her translating helping..
.
Bir önceki yazımız olan Yolda bulduğumuz telefonu güvenlik açığından yararlanarak sahibine nasıl ulaştırdık? başlıklı makalemizi de okumanızı öneririz.
 Sahin SOLMAZ - Versatile Web Developer - Cyber Security Enthusiast
Sahin SOLMAZ - Versatile Web Developer - Cyber Security Enthusiast