after a long time hi again everyone!
recently, one of my friend has needed to test an Android application as detailed (checking its API requests). and asked me this need’s solution. then I did a test for SSL pinning bypass for an Android application on Windows with Frida. now I will explain all steps here for you.
just a short summary for SSL Pinning:
If the mobile application does not have SSL pinning, the attackers can read the HTTP packets going back and forth between the application and the server over the network with a proxy easly. For this stiation, the SSL pinning method is used, as a precaution. and as with everything, there are some solutions to bypass. we use Frida for SSL pinning bypass in this article. now let’s start!
requirements first:
- Fiddler (Classic or Everywhere),
- Python,
- Frida,
- Genymotion / Emulator or any other,
- ADB – Android Debug Bridge (if you prefer Genymotion, it already has adb tool.)
start:
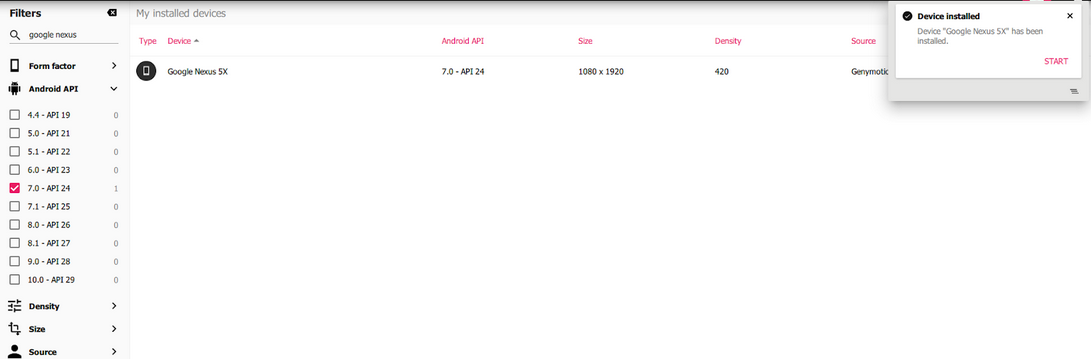
- Install the emulator, and setup an Android
(I used Genymotion and Android 7 – Google Nexus)
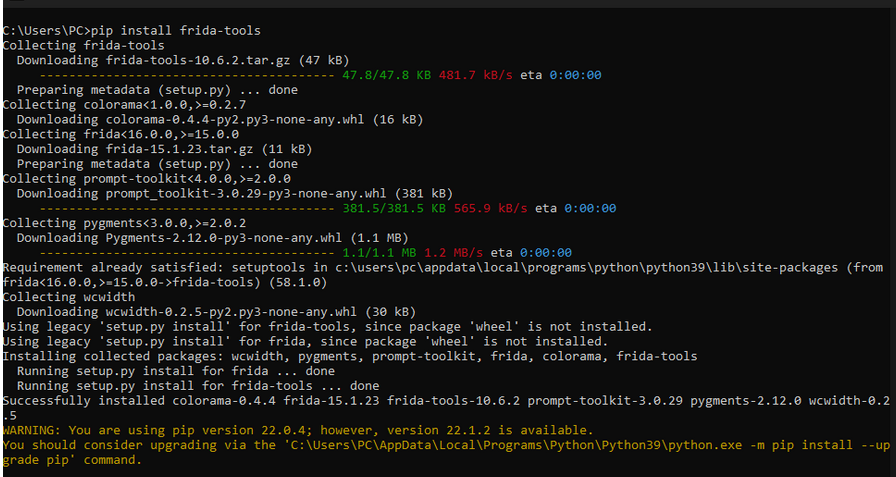
- Install Frida look here for details,
- Install Fiddler Classic and Python if you don’t have them,
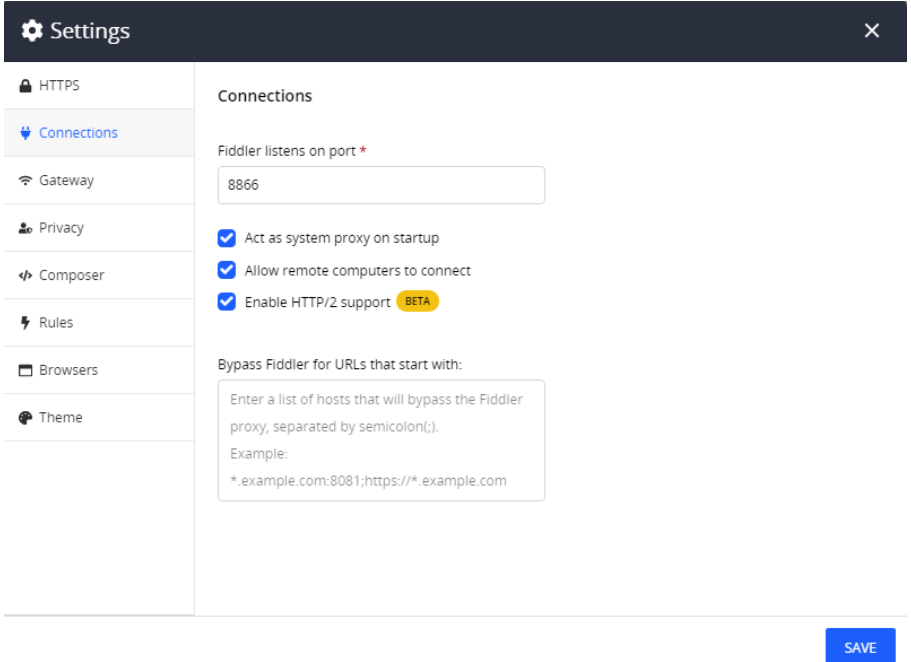
// Not that Fiddler’s default port is 8888. Set a port number and use it on everwhere.
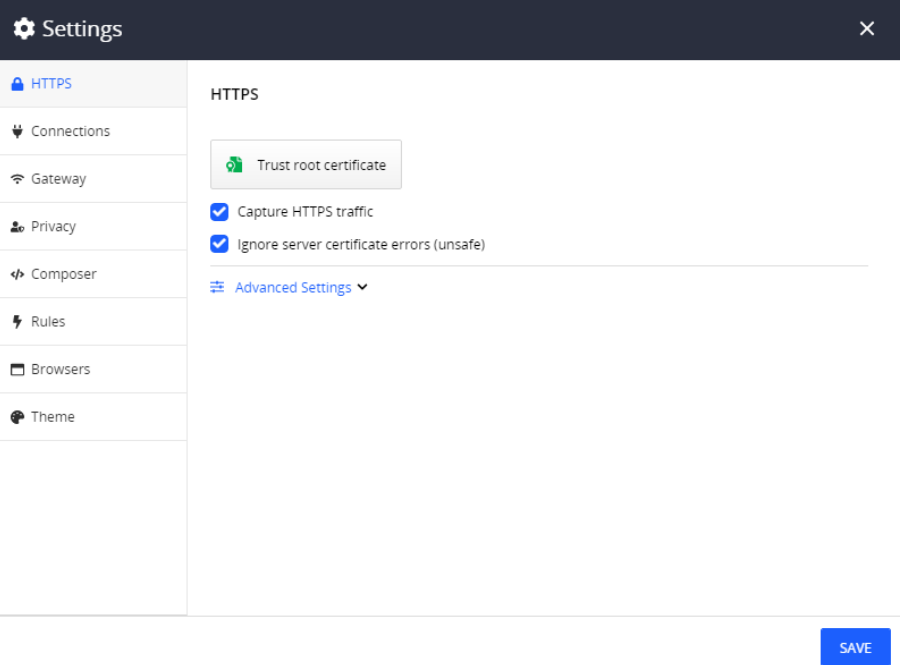
// General settings for Fiddler SSL tab.
Action:
- Run your Android,
- Connect your WiFi,
- (if you need) Download OpenGAPPs:
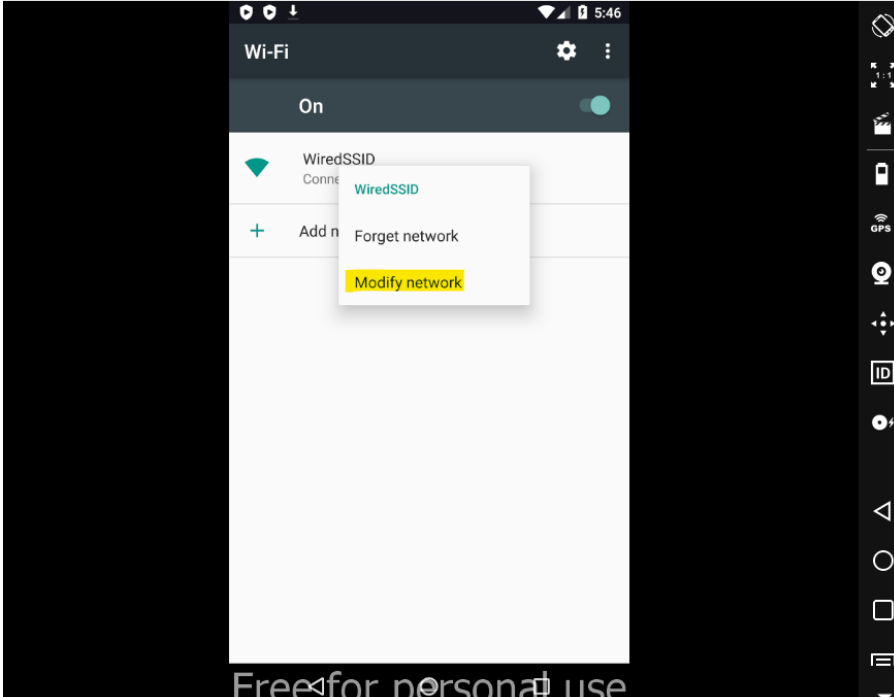
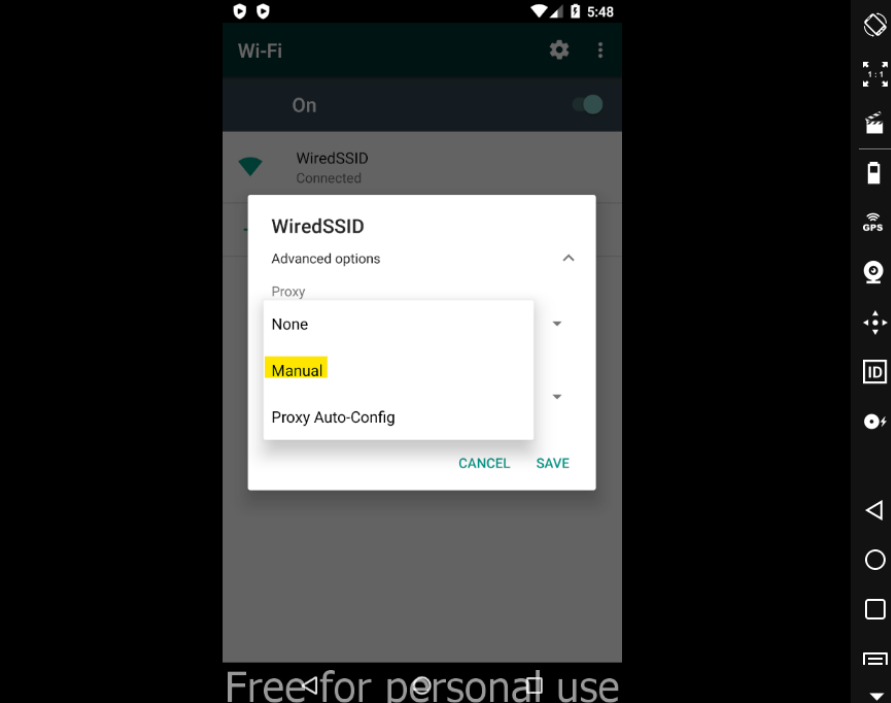
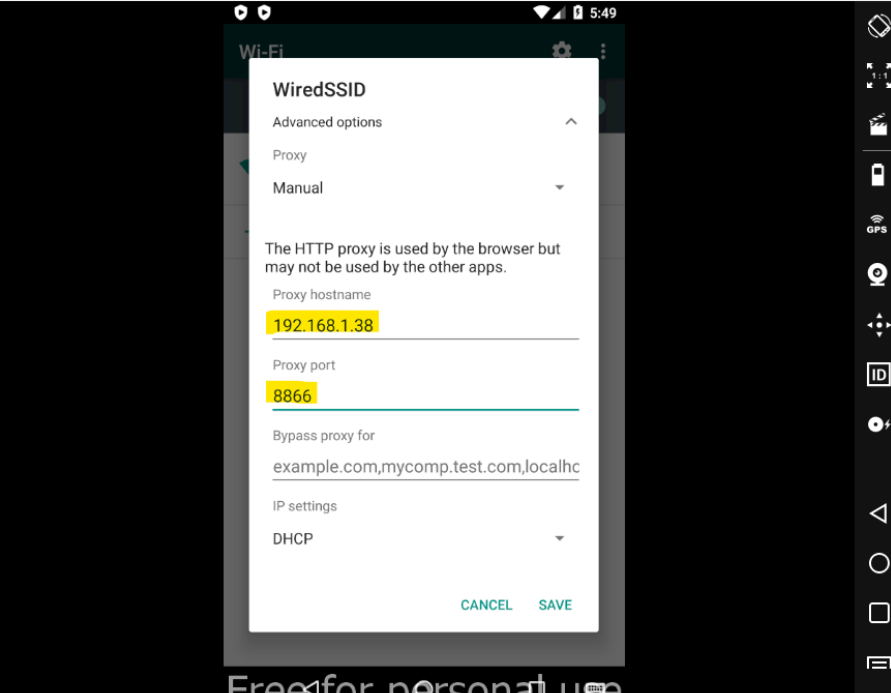
- Set your proxy settings on your WiFi connection,
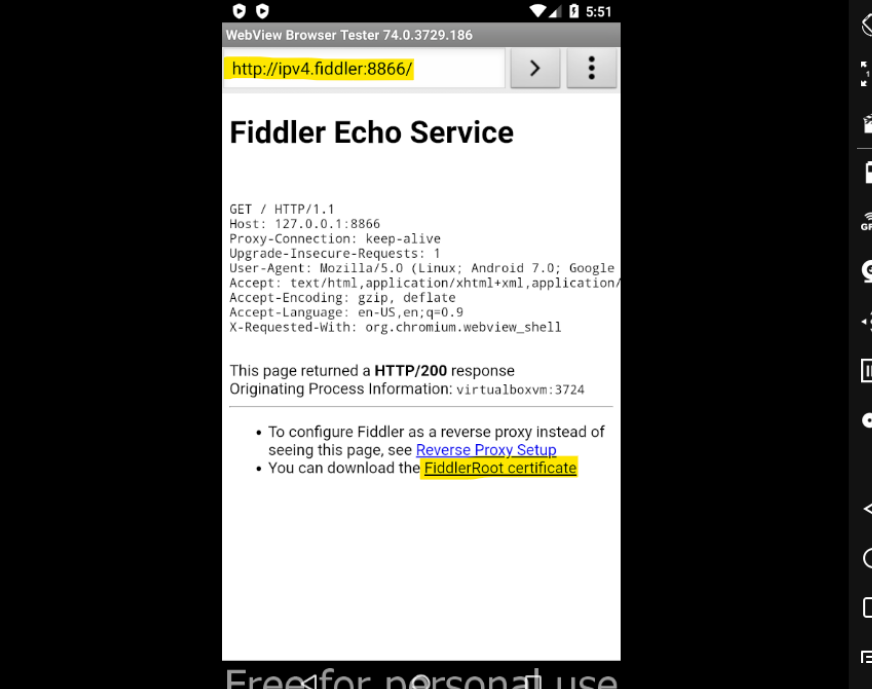
- Open your mobile browser and visit: http://ipv4.fiddler:8888 (replace 8888, with your port)
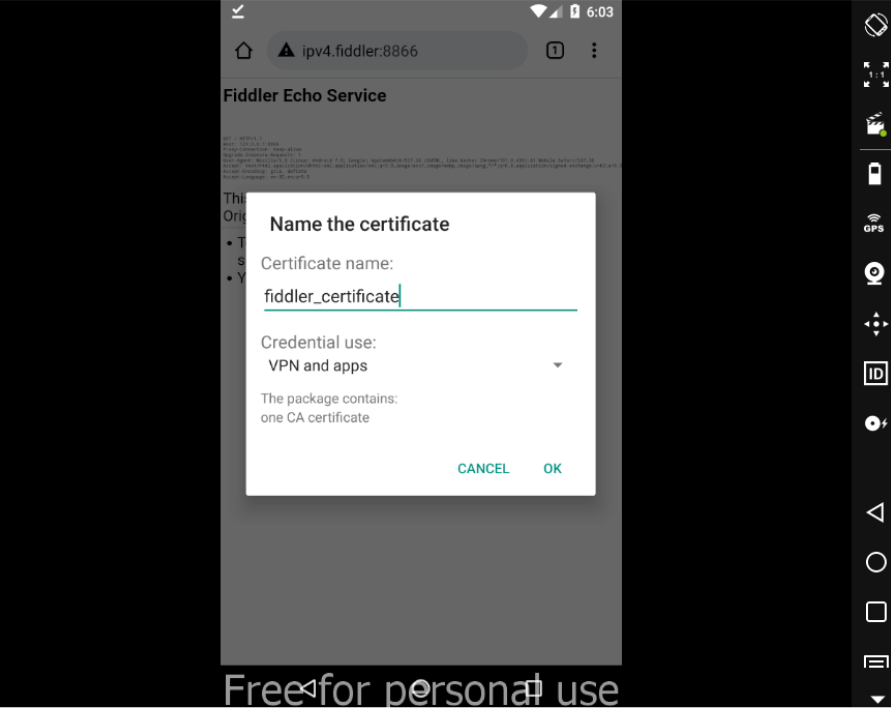
- Download FiddlerRoot cert and install it.
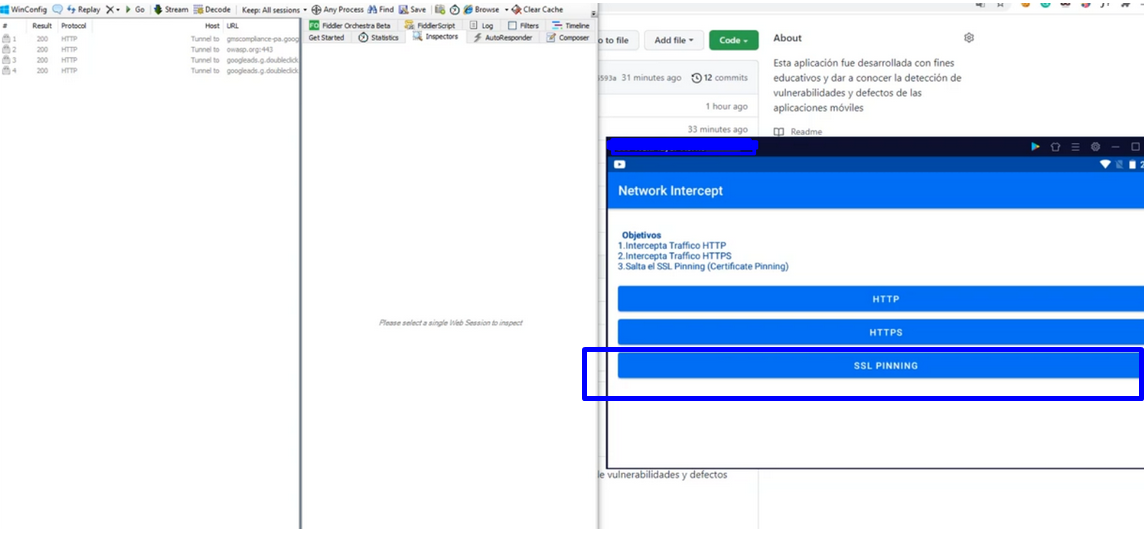
- Download PAPARAZZIAPPS [SECURITY APP] – APK to test SSL Pinning from here:
https://github.com/ahuamana/SecurityApp/releases/download/1.4/PaparazzyApps.-.SecurityApp.apk - Install this APK to your Android device, and open it (to test http and https click them),
And the main details:
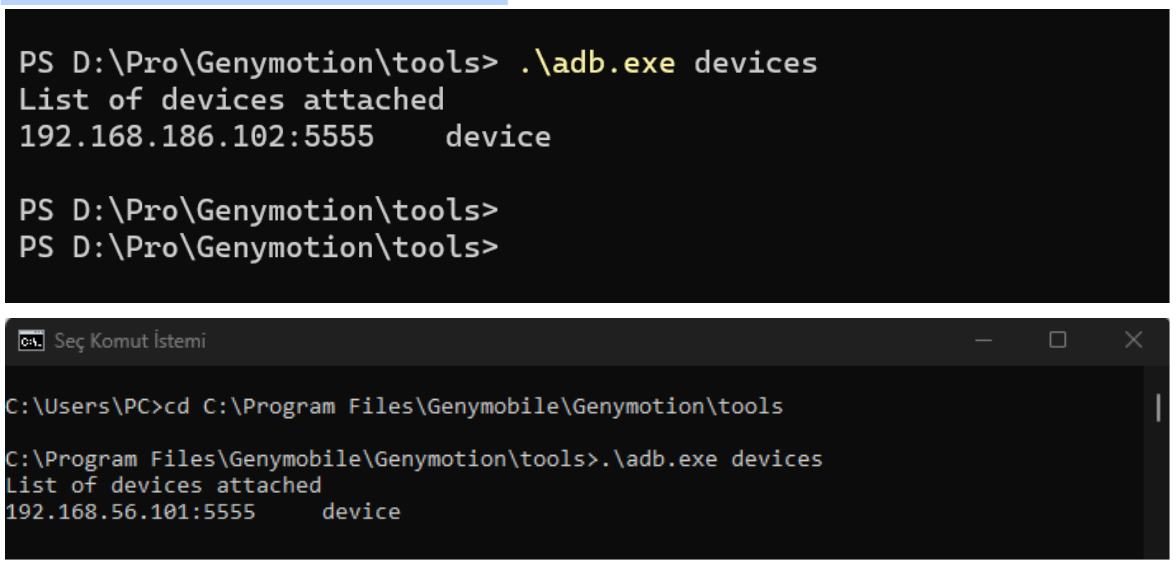
- Go to your emulator folder which has adb.exe and open terminal for this folder,
- run:
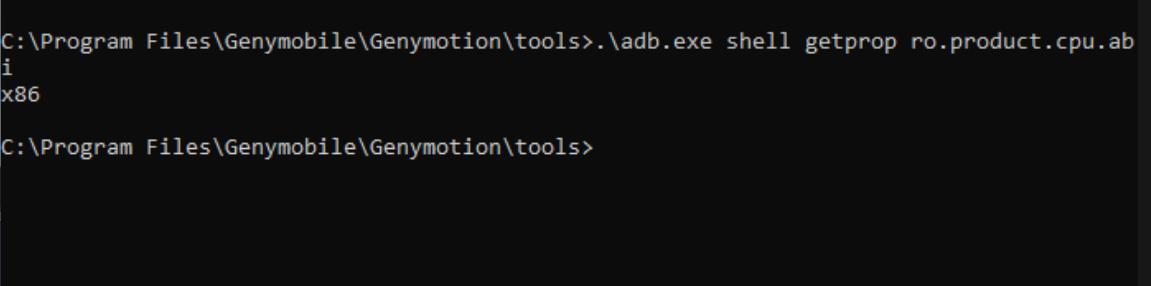
# .\adb.exe devices (to see your device) - and run the below code to get your Android device core type info
# .\adb.exe shell getprop ro.product.cpu.abi
the output should like this: x86:
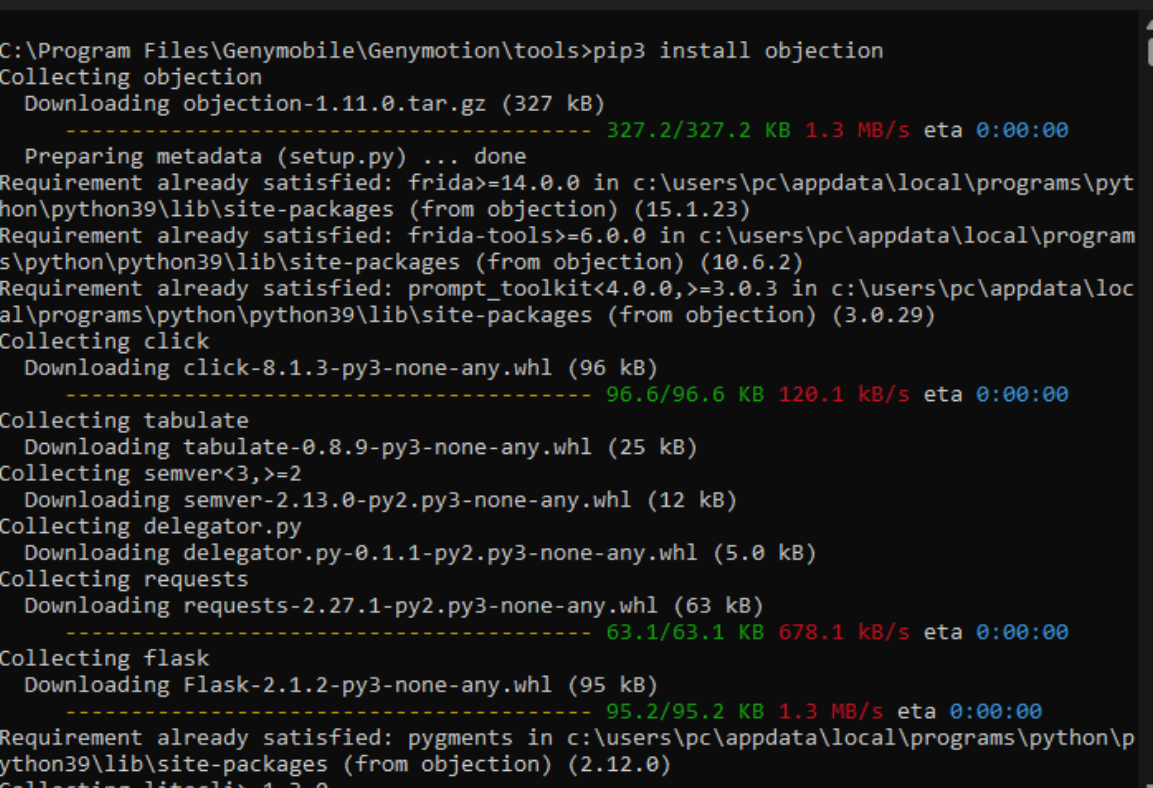
- and let’s install the objection
# pip3 install objection// Objection is a runtime mobile exploration toolkit. developed by frida.
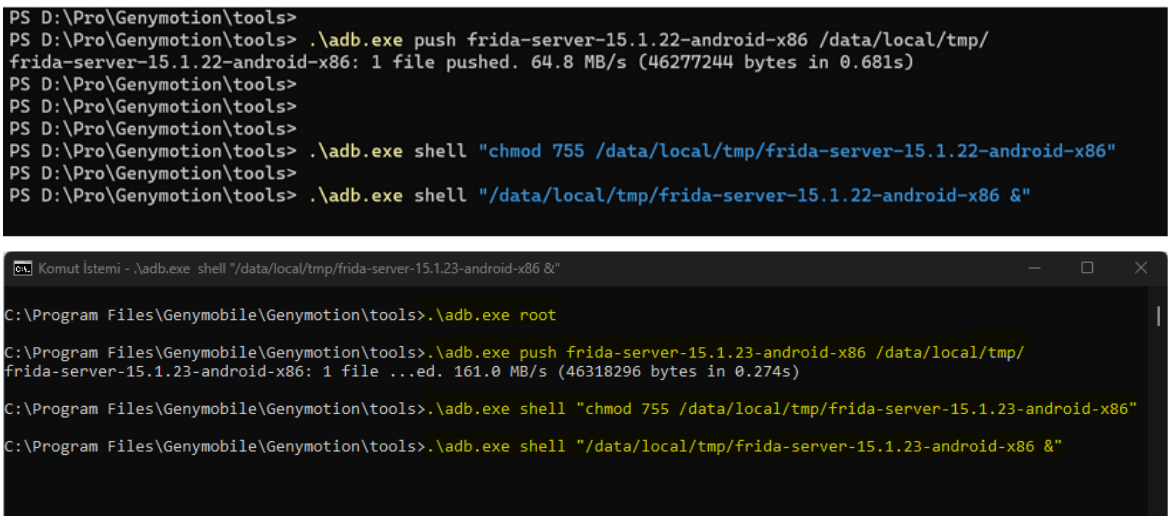
- Go to Frida releases and download your frida-server which is okay with your Android version from here: https://github.com/frida/frida/releases
i.e: frida-server-15-1.22-android-x86 is mine. - Unzip and copy your frida-server to adb.exe folder, in this folder, run these:
- # .\adb.exe root
- # .\adb.exe push frida-server-15.1.23-android-x86 /data/local/tmp/
- # .\adb.exe shell “chmod 755 /data/local/tmp/frida-server-15.1.23-android-x86”
and the big moment:
time to bigbang!
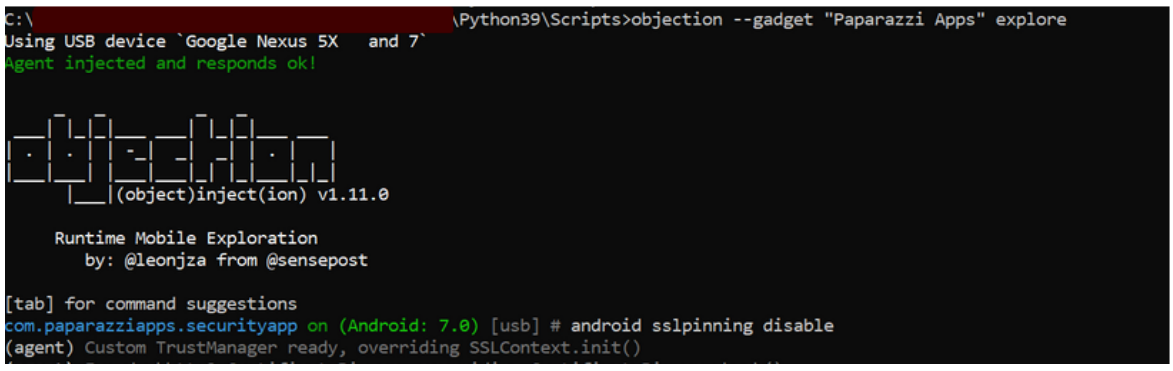
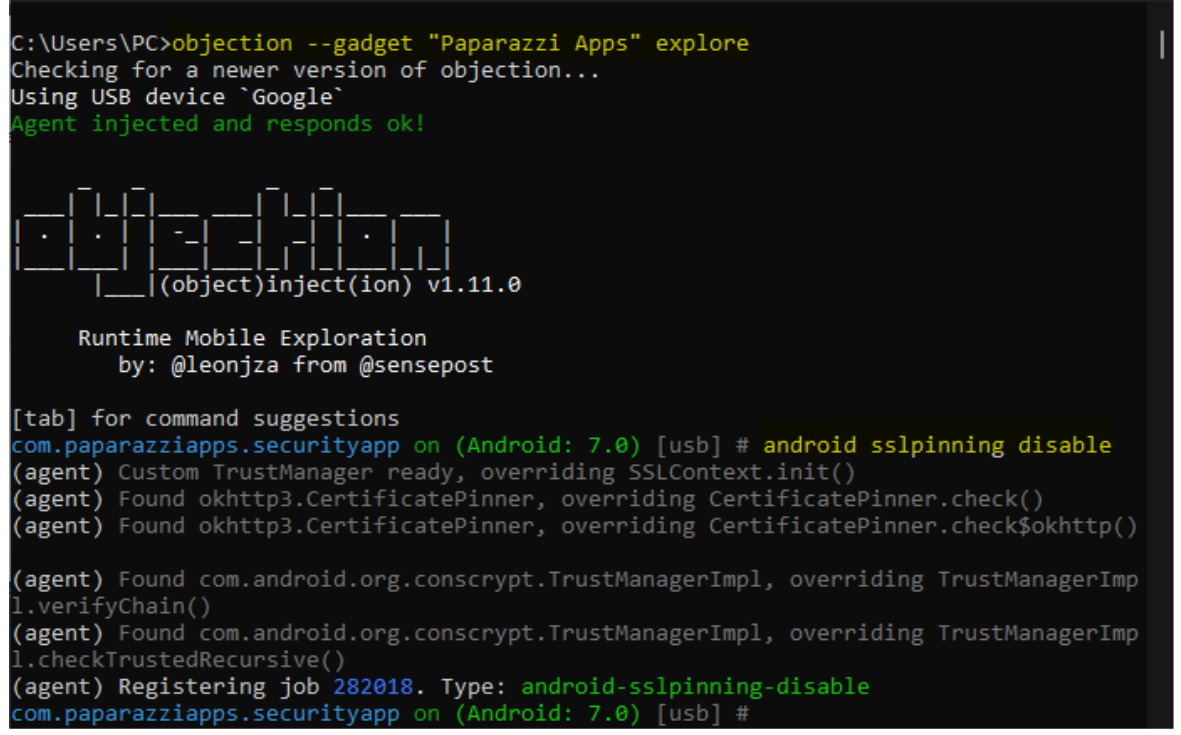
and now retest to SSL Pinning and to get success result:
and done! =)
Even though the mobile application SSL Pinning, we can catch requests now.
Thanks a lot to Ms. Aysenur Burak for retesting this article.
Bir önceki yazımız olan SMTP (Yandex, Gmail vd) Mail Gönderim hatalarına farklı bir bakış: başlıklı makalemizi de okumanızı öneririz.
 Sahin SOLMAZ - Versatile Web Developer - Cyber Security Enthusiast
Sahin SOLMAZ - Versatile Web Developer - Cyber Security Enthusiast